Table of contents
Open Table of contents
Intro
In this post, there will be a set of TLDRs (too long; didn’t read) for categorized Penetration Testing tools.
I recommend a command line tool called tldr:
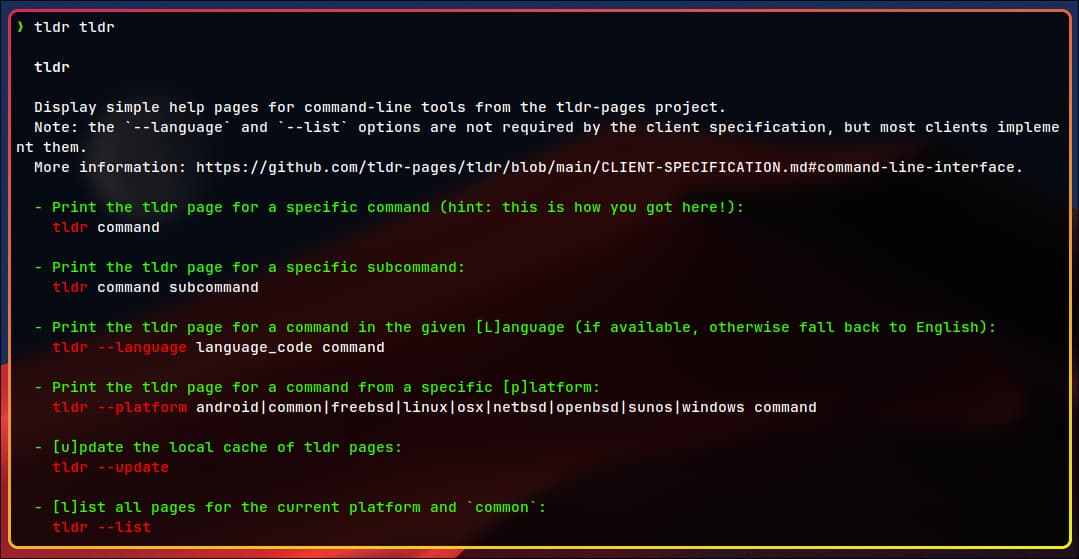
While I was preparing the article, I contributed to some tldr pages:
- netdiscover
- …
TLDRs
Network Scanning
nmap
It is a Network exploration tool and security/port scanner.
# Scan all TCP ports (1–65535) with timing option <T> and verbose
nmap -p- -T<T> <IP-or-HOSTNAME> -v
# Example: nmap -p- -T4 192.168.1.10 -v
# TCP SYN scan on specific ports (e.g., 80 and 3306–5555)
sudo nmap -sS -p<port1>,<port_range> -T<T> <IP> -v
# Example: sudo nmap -sS -p80,3306-5555 -T4 10.0.0.5 -v
# In-depth scan on specific ports with service and script detection
nmap -p<port1>,<port2> -sS -sC -sV <IP> -vv
# Example: nmap -p22,80 -sS -sC -sV 192.168.1.1 -vv
# Fast scan with minimum packet rate <rate>
nmap -p- -sS -sC -sV <IP> -v --min-rate <rate>
# Example: nmap -p- -sS -sC -sV 10.0.0.5 -v --min-rate 10000
# Run a specific NSE script (e.g., smb-flood)
nmap -p<port> --script=<script>.nse <IP>
# Example: nmap -p445 --script=smb-flood.nse 192.168.1.100
# Run all scripts matching a pattern on multiple hosts
nmap -p<port> --script=<pattern> <IP1>,<IP2>,<IP3>
# Example: nmap -p445 --script=smb-* 192.168.1.10,192.168.1.11
# Output results in all formats: -oA <prefix>
nmap -oA <output_prefix> <IP>
# Example: nmap -oA fullscan 192.168.1.1
# Scan targets from input file
nmap -iL <file>
# Example: nmap -iL targets.txt
fping
A Network Discovery tool to ping multiple hosts.
# Get alive hosts (-a) within Network (-g) with cumulative output (-s) and quiet (-q)
fping -asgq <IP/N>
# Example: 192.168.1.1/24
# Get alive hosts between <IP-A> and <IP-B>
fping -asgq IP-A IP-B
# Example: 192.168.1.1 192.168.1.254
netdiscover
A Network Discovery tool
# Get alive hosts in an IP range (-r) and from certain interface (-i)
netdiscover -r <IP/N> -i <network-interface>
# Example: -r 172.16.6.0/23 -i ens244
Web Application Testing
dirb
A tool to scan directories on websites.
# Scan a website
dirb <url>
# Example: https://elnurbda.com
# Use a specific wordlist
dirb <url> <wordlist>
# Example: https://elnurbda.com ./wordlist.txt
# Some useful options for Scan
# -a <agent_string>
# -r : Don't search recursively.
# -R : Interactive recursion. (Asks for each directory)
# -u <username:password> : HTTP Authentication.
# -X <extensions> / -x <exts_file> : Append each word with this extensions.
# -z <milisecs> : Add a miliseconds delay to not cause excessive Flood.
dirbuster
A tool to brute-force directories and files on web servers.
# Start DirBuster in GUI mode with a target URL
dirbuster -u <url>
# Example: -u elnurbda.com
# Start in headless mode (-H), auto-saves report on exit
dirbuster -H -u <url>
# Example: -u elnurbda.com
# Use a specific wordlist (-l), set number of threads (-t), and extensions (-e)
dirbuster -H -u <url> -l <wordlist.txt> -t <number> -e <ext1,ext2>
# Example: -u http://elnurbda.com -l ./wordlist.txt -t 20 -e php,txt,html
# Run scan without parsing HTML (-P), disable recursion (-R), and use only GET (-g)
dirbuster -H -u <url> -P -R -g
# Example: -u http://elnurbda.com -P -R -g
# Set custom start path (-s) and save report to specific file (-r)
dirbuster -H -u <url> -s </path> -r <filename>
# Example: -u http://elnurbda.com -s /admin -r ./report.txt
# Enable verbose output
dirbuster -v
gobuster
A tool to brute-force directories, subdomains, VHOSTs, S3 buckets, and more.
# Discover directories and files on a website
gobuster dir -u <url> -w <wordlist>
# Example: -u https://elnurbda.com -w ./common.txt
# Discover subdomains of a domain
gobuster dns -d <domain> -w <wordlist>
# Example: -d elnurbda.com -w ./subdomains.txt
# Discover virtual hosts (VHOSTs) on a server
gobuster vhost -u <url> -w <wordlist>
# Example: -u http://elnurbda.com -w ./vhosts.txt
# Fuzz the value of a parameter using FUZZ keyword
gobuster fuzz -u "<url>?param=FUZZ" -w <wordlist>
# Example: -u "http://elnurbda.com/page?view=FUZZ" -w ./payloads.txt
# Fuzz the name of a parameter
gobuster fuzz -u "<url>?FUZZ=value" -w <wordlist>
# Example: -u "http://elnurbda.com/page?FUZZ=value" -w ./params.txt
# Discover Amazon S3 buckets
gobuster s3 -w <wordlist>
# Example: -w ./buckets.txt
# Common options for tuning
# -t <threads> Set number of threads (default: 10)
# -o <file> Save output to a file
# -q Quiet mode (suppress banner/info)
# -v Verbose (show errors)
# --delay <ms> Add delay between requests (e.g., 500ms)
ffuf
A fast web fuzzer written in Go. Use FUZZ as a placeholder in the URL, headers, or data to inject words from a wordlist.
# Discover directories and files using FUZZ keyword
ffuf -w <wordlist> -u <url>/FUZZ -c
# Example: -w ./dirs.txt -u https://elnurbda.com/FUZZ -c
# Fuzz subdomains by placing FUZZ in the hostname
ffuf -w <wordlist> -u http://FUZZ.elnurbda.com
# Example: -w ./subdomains.txt -u http://FUZZ.elnurbda.com
# Fuzz with POST data and specific HTTP method
ffuf -w <wordlist> -X POST -d "user=admin&pass=FUZZ" -u <url> -fc 401,403
# Example: -u http://elnurbda.com/login -X POST -d "u=admin&p=FUZZ" -w ./passwords.txt -fc 403
# Fuzz a specific header (e.g. Host) and match status code 200
ffuf -w <wordlist> -u <url> -H "Host: FUZZ" -mc 200
# Example: -u http://192.168.1.1 -w ./vhosts.txt -H "Host: FUZZ" -mc 200
# Use a proxy and set threads
ffuf -w <wordlist> -u <url>/FUZZ -x http://127.0.0.1:8080 -t 100
# Example: -w ./dirs.txt -u http://elnurbda.com/FUZZ -x http://127.0.0.1:8080 -t 100
dirsearch
A web path scanner. Bruteforces directories and files on web servers using wordlists and extensions.
# Basic scan: use default wordlist with common extensions
dirsearch -u <url> -e <extensions>
# Example: dirsearch -u https://elnurbda.com -e php,html,js
# Use custom wordlists
dirsearch -u <url> -e <extensions> -w <wordlist1>,<wordlist2>
# Example: dirsearch -u https://elnurbda.com -e php -w ./api.txt,./admin.txt
# Scan a list of targets (one per line in file)
dirsearch -l <targets.txt> -e php,aspx
# Example: -l ./hosts.txt -e php
# Use a cookie for authentication
dirsearch -u <url> -e <extensions> --cookie="SESSIONID=abc123"
# Example: dirsearch -u https://elnurbda.com -e html --cookie="auth=token"
# Use the HEAD method instead of GET
dirsearch -u <url> -e <extensions> -m HEAD
# Example: dirsearch -u https://elnurbda.com -e php -m HEAD
# Save results to a JSON report
dirsearch -u <url> -e php --format json -o ./output.json
# Example: dirsearch -u https://elnurbda.com -e php --format json -o results.json
# Recursive scan with max depth
dirsearch -u <url> -e php -r -R 3
# Example: dirsearch -u https://elnurbda.com -e php -r -R 3
# Use proxy (e.g. Burp Suite)
dirsearch -u <url> -e php --proxy http://127.0.0.1:8080
# Example: dirsearch -u http://elnurbda.com -e php --proxy http://127.0.0.1:8080
# Exclude status codes and sizes
dirsearch -u <url> -e php -x 403,404 --exclude-sizes 0B,1KB
wfuzz
A flexible web application fuzzer for brute-forcing parameters, directories, logins, and more.
# Fuzz directories/files using a wordlist
wfuzz -w <path/to/wordlist> <url>/FUZZ
# Example: wfuzz -w ./common.txt https://elnurbda.com/FUZZ
# Use a proxy while fuzzing
wfuzz -w <path/to/wordlist> -p <ip:port:type> <url>/FUZZ
# Example: wfuzz -w ./dirs.txt -p 127.0.0.1:8080:HTTP https://elnurbda.com/FUZZ
# Save results to file using a specific format (printer)
wfuzz -w <wordlist> -f <filename>,<printer> <url>/FUZZ
# Example: wfuzz -w ./list.txt -f output.json,json https://elnurbda.com/FUZZ
# Colorized output and filter only specific status codes
wfuzz -c -w <wordlist> --sc <status_codes> <url>/FUZZ
# Example: wfuzz -c -w ./web.txt --sc 200,301,302 https://elnurbda.com/FUZZ
# Fuzz virtual hosts via Host header; hide responses and set thread count
wfuzz -w <vhosts.txt> -H "Host: FUZZ.<domain>" --hc <codes> --hw <words> -t <threads> <url>
# Example: wfuzz -w ./subs.txt -H "Host: FUZZ.elnurbda.com" --hc 301 --hw 222 -t 100 elnurbda.com
# Brute-force HTTP Basic Auth using 2 wordlists (user:pass)
wfuzz -c --hc <fail_code> -z file,<userlist> -z file,<passlist> --basic 'FUZZ:FUZ2Z' <url>
# Example: wfuzz -c --hc 401 -z file,users.txt -z file,passwords.txt --basic 'FUZZ:FUZ2Z' https://elnurbda.com
# Inline wordlist for quick payload testing using POST data
wfuzz -z list,<item1>-<item2>-<item3> <url> -d "<POST_param>=FUZZ"
# Example: wfuzz -z list,alpha-beta-gamma https://elnurbda.com -d "id=FUZZ"
# Encode payload using encoders (e.g., base64, md5)
wfuzz -z file,<path>,<encoders> <url>/FUZZ
# Example: wfuzz -z file,./keys.txt,base64-md5 https://elnurbda.com/FUZZ
# Set custom HTTP method
wfuzz -X <method> -w <wordlist> <url>/FUZZ
# Example: wfuzz -X HEAD -w ./urls.txt https://elnurbda.com/FUZZ
# Use cookies while fuzzing
wfuzz -b "<cookie>" -w <wordlist> <url>/FUZZ
# Example: wfuzz -b "session=abc123; user=admin" -w ./admin.txt https://elnurbda.com/FUZZ
# Use multiple headers (repeat -H)
wfuzz -H "<Header1>" -H "<Header2>" -w <wordlist> <url>/FUZZ
# Example: wfuzz -H "User-Agent: fuzzAgent" -H "X-Test: FUZZ" -w ./payloads.txt https://elnurbda.com/FUZZ
# Delay between requests to avoid rate-limiting
wfuzz -s <seconds> -w <wordlist> <url>/FUZZ
# Example: wfuzz -s 2 -w ./api.txt https://elnurbda.com/FUZZ
# Set timeout for connection or request
wfuzz --conn-delay <seconds> --req-delay <seconds> -w <wordlist> <url>/FUZZ
# Example: wfuzz --conn-delay 5 --req-delay 10 -w ./api.txt https://elnurbda.com/FUZZ
# Follow HTTP redirects
wfuzz -L -w <wordlist> <url>/FUZZ
# Example: wfuzz -L -w ./paths.txt https://elnurbda.com/FUZZ
# Hide responses based on HTTP status, length, word count, headers
wfuzz --hc <codes> --hl <lines> --hw <words> --hh <chars> -w <wordlist> <url>/FUZZ
# Example: wfuzz --hc 404,403 --hw 25 -w ./web.txt https://elnurbda.com/FUZZ
# Show only responses that match filter (status, words, regex)
wfuzz --sc <codes> --ss <regex> -w <wordlist> <url>/FUZZ
# Example: wfuzz --sc 200 --ss "admin" -w ./pages.txt https://elnurbda.com/FUZZ
# Use pre-defined scripts (like nmap NSE-style plugins)
wfuzz --script=<plugin> -w <wordlist> <url>/FUZZ
# Example: wfuzz --script=discover -w ./api.txt https://elnurbda.com/FUZZ
# List available encoders/payloads/etc
wfuzz -e <type>
# Example: wfuzz -e encoders
nikto
A web server vulnerability scanner that tests for outdated software, config issues, and known exploits.
# Run a basic scan on a target host
nikto -host <ip_or_domain>
# Example: nikto -host elnurbda.com
# Scan a specific port
nikto -host <ip_or_domain> -port <port>
# Example: nikto -host elnurbda.com -port 443
# Use full URL with protocol and port
nikto -host <full_url>
# Example: nikto -host https://elnurbda.com:8443/
# Scan multiple ports in one session
nikto -host <ip_or_domain> -port <port1,port2,...>
# Example: nikto -host elnurbda.com -port 80,443,8080
# Enable SSL manually (useful for non-443 HTTPS)
nikto -host <ip_or_domain> -ssl
# Example: nikto -host elnurbda.com -ssl
# Save results to a file (auto-name)
nikto -host <ip_or_domain> -output .
# Example: nikto -host elnurbda.com -output .
# Save results with specific format
nikto -host <ip_or_domain> -output <filename> -Format <format>
# Example: nikto -host elnurbda.com -output results.json -Format json
# Use proxy (from config or inline)
nikto -host <ip_or_domain> -useproxy <proxy_url>
# Example: nikto -host elnurbda.com -useproxy http://127.0.0.1:8080
# Update plugins and databases
nikto -update
# Example: nikto -update
# Use tuning to focus on specific tests
nikto -host <ip_or_domain> -Tuning <numbers>
# Example: nikto -host elnurbda.com -Tuning 1,2,4,9
# Use authentication
nikto -host <ip_or_domain> -id <user:pass>
# Example: nikto -host elnurbda.com -id admin:admin123
# Set a custom User-Agent
nikto -host <ip_or_domain> -useragent "<user_agent_string>"
# Example: nikto -host elnurbda.com -useragent "NiktoScanner/1.0"
# Ignore certain HTTP response codes or body content
nikto -host <ip_or_domain> -404code <codes> -404string <string>
# Example: nikto -host elnurbda.com -404code 403,404 -404string "Not Found"
# Enable verbose/debug output
nikto -host <ip_or_domain> -Display <flags>
# Example: nikto -host elnurbda.com -Display V
# Limit scan time per host
nikto -host <ip_or_domain> -maxtime <time>
# Example: nikto -host elnurbda.com -maxtime 10m
cewl
URL spidering tool that creates custom wordlists from website content for password cracking.
# Generate a wordlist by crawling a site up to a specified depth and save output to a file
cewl -d <depth> -w <output_file> <url>
# Example: cewl -d 2 -w wordlist.txt https://elnurbda.com
# Generate a wordlist with words of minimum length and including numbers
cewl --with-numbers -m <min_word_length> <url>
# Example: cewl --with-numbers -m 5 https://elnurbda.com
# Generate a wordlist with email addresses and debug output
cewl -e --debug <url>
# Example: cewl -e --debug https://elnurbda.com
# Generate a wordlist using HTTP Basic or Digest authentication
cewl --auth_type <basic|digest> --auth_user <username> --auth_pass <password> <url>
# Example: cewl --auth_type basic --auth_user admin --auth_pass secret https://elnurbda.com
# Generate a wordlist through a proxy
cewl --proxy_host <proxy_host> --proxy_port <proxy_port> <url>
# Example: cewl --proxy_host 127.0.0.1 --proxy_port 8080 https://elnurbda.com
Password Cracking
hydra
Online password guessing tool for cracking login/password pairs across many protocols.
# Guess SSH credentials with a single username and a password list
hydra -l <username> -P <password_list> <host> ssh
# Example: hydra -l admin -P /path/to/passlist.txt elnurbda.com ssh
# Guess HTTPS form login credentials with username and password lists and custom post data
hydra -L <user_list> -P <pass_list> <host> https-post-form "<url_path>:<post_data>:<failure_string>"
# Example: hydra -L users.txt -P pass.txt elnurbda.com https-post-form "/login.php:username=^USER^&password=^PASS^:Login failed"
# Guess FTP credentials with username and password lists and multiple parallel tasks
hydra -L <user_list> -P <pass_list> -t <num_tasks> <host> ftp
# Example: hydra -L users.txt -P passwords.txt -t 16 elnurbda.com ftp
# Guess MySQL credentials with a username and password list, stop after first success
hydra -l <username> -P <pass_list> -f <host> mysql
# Example: hydra -l root -P passlist.txt -f elnurbda.com mysql
# Guess POP3 credentials on multiple hosts, stop after first success per host
hydra -L <user_list> -P <pass_list> -M <host_list> -F pop3
# Example: hydra -L users.txt -P pass.txt -M targets.txt -F pop3
john
John the Ripper – password hash cracker for many formats.
# Crack hashes in a file
john <hashes_file>
# Example: john hashes.txt
# Show cracked passwords from a hashes file
john --show <hashes_file>
# Example: john --show hashes.txt
# Crack hashes using a custom wordlist
john --wordlist=<wordlist_file> <hashes_file>
# Example: john --wordlist=wordlist.txt hashes.txt
# Crack hashes using specific hash format (e.g. md5crypt)
john --format=md5crypt <hashes_file>
# Example: john --format=md5crypt hashes.txt
# Enable word mangling rules during cracking
john --rules <hashes_file>
# Example: john --rules hashes.txt
# Restore an interrupted cracking session
john --restore=<session_name>
# Example: john --restore=mycrack
# List available hash formats
john --list=formats
Wireless Security
Aircrack-ng Toolset
airmon-ng
It manages monitor mode for wireless devices.
# List wireless devices and their statuses
sudo airmon-ng
# Start monitor mode on a wireless interface
sudo airmon-ng start <interface>
# Example: sudo airmon-ng start wlan0
# Kill processes that interfere with wireless devices
sudo airmon-ng check kill
# Stop monitor mode on a wireless interface
sudo airmon-ng stop <interface>
# Example: sudo airmon-ng stop wlan0mon
airodump-ng
It capture packets and display information about wireless networks.
# Capture packets and show wireless networks on the 2.4GHz band
sudo airodump-ng <interface>
# Example: sudo airodump-ng wlan0mon
# Capture packets on the 5GHz band
sudo airodump-ng --band a <interface>
# Example: sudo airodump-ng --band a wlan0mon
# Capture packets on both 2.4GHz and 5GHz bands
sudo airodump-ng --band abg <interface>
# Example: sudo airodump-ng --band abg wlan0mon
# Capture packets on a specific channel, targeting a BSSID, and save the output
sudo airodump-ng --channel <channel> --bssid <bssid> --write <file_prefix> <interface>
# Example: sudo airodump-ng --channel 6 --bssid AA:BB:CC:DD:EE:FF --write capture wlan0mon
# Capture and save in multiple formats (e.g., pcap and csv)
sudo airodump-ng --write <file_prefix> --output-format pcap,csv <interface>
# Example: sudo airodump-ng --write dump --output-format pcap,csv wlan0mon
# Use specific hopping frequencies in MHz
sudo airodump-ng -C <frequencies> <interface>
# Example: sudo airodump-ng -C 2412,2437,2462 wlan0mon
aireplay-ng
It injects custom packets into wireless networks to perform various attacks.
# Deauthenticate a specific client from an access point
sudo aireplay-ng --deauth <count> --bssid <ap_mac> --dmac <client_mac> <interface>
# Example: sudo aireplay-ng --deauth 10 --bssid AA:BB:CC:DD:EE:FF --dmac 11:22:33:44:55:66 wlan0mon
# Deauthenticate all clients from an access point
sudo aireplay-ng --deauth <count> --bssid <ap_mac> <interface>
# Example: sudo aireplay-ng --deauth 50 --bssid AA:BB:CC:DD:EE:FF wlan0mon
# Fake authentication with an access point
sudo aireplay-ng --fakeauth <delay> -a <ap_mac> -h <your_mac> <interface>
# Example: sudo aireplay-ng --fakeauth 0 -a AA:BB:CC:DD:EE:FF -h 11:22:33:44:55:66 wlan0mon
# Perform ARP replay attack to inject traffic and capture IVs
sudo aireplay-ng --arpreplay -b <ap_mac> -h <your_mac> <interface>
# Example: sudo aireplay-ng --arpreplay -b AA:BB:CC:DD:EE:FF -h 11:22:33:44:55:66 wlan0mon
# Perform fragmentation attack to generate a keystream
sudo aireplay-ng --fragment -b <ap_mac> -h <your_mac> <interface>
# Example: sudo aireplay-ng --fragment -b AA:BB:CC:DD:EE:FF -h 11:22:33:44:55:66 wlan0mon
# Perform interactive packet selection mode
sudo aireplay-ng --interactive -b <ap_mac> -h <your_mac> <interface>
# Example: sudo aireplay-ng --interactive -b AA:BB:CC:DD:EE:FF -h 11:22:33:44:55:66 wlan0mon
aircrack-ng
It cracks WEP and WPA/WPA2 keys from packet capture files using wordlists or statistical attacks.
# Crack WPA/WPA2 key from a capture file using a wordlist
aircrack-ng -w <wordlist> <capture_file>
# Example: aircrack-ng -w rockyou.txt capture.cap
# Crack WPA/WPA2 key with a wordlist and specify the ESSID
aircrack-ng -w <wordlist> -e <essid> <capture_file>
# Example: aircrack-ng -w rockyou.txt -e MyWiFi capture.cap
# Crack WPA/WPA2 key with a wordlist and specify the BSSID
aircrack-ng -w <wordlist> --bssid <bssid> <capture_file>
# Example: aircrack-ng -w rockyou.txt --bssid AA:BB:CC:DD:EE:FF capture.cap
# Crack WEP key using statistical attack on a capture file
aircrack-ng <capture_file>
# Example: aircrack-ng capture.ivs
# Crack WEP key using PTW method and a limited number of IVs
aircrack-ng -n 128 -M 10000 <capture_file>
# Example: aircrack-ng -n 128 -M 10000 capt
Exploitation Frameworks
msfconsole
powershell-empire
Reverse Engineering
Privilege Escalation
linpeas, winpeas
Conclusion
I believe this article will be useful for Cyber Security Enthusiasts, and way more useful than one of my previous articles:
- Pentester’s Notes - A comprehensive collection of penetration testing commands and techniques
Note! It was over to the point and lacked a lot of information.
Another Note! The article is incomplete and the list will cover more tools.